Last Friday we witnessed the start of what has been one of the biggest worldwide cyber attacks in history, the WannaCry malware attack. While information security and hacking threats in general receive regular coverage in the news and media, we haven’t seen anything like the coverage around the WannaCry malware attack recently. Not since the Sony Playstation hack in 2011 have we seen as much media interest in a hacking event. News outlets cover hacking stories quite frequently because they pose this kind of threat to people. However, when we look at the news coverage over the course of the past 12 months in the graph below, we can see that triple the average monthly story volume on malware was produced in the first three days of the attack alone. In this blog, we’ll use our News API to look at the media coverage of WannaCry before the news of the attack broke and afterwards, as details of the attack began to surface.
Monthly count of articles mentioning “malware” or “ransomware” over the last 12 months
By analyzing the news articles published about WannaCry and malware in general, with the help of some visualizations we’re going to look at three aspects:
- warning signs in the content published before the attack;
- how the story developed in the first days of the attack;
- how the story spread across social media channels.
WannaCry
At 8am CET on Friday May 12th, the WannaCry attack began, and by that evening it had infected over 50,000 machines in 70 countries. By the following Monday, that had risen to 213,000 infections, paralyzing computer systems in hospitals, factories, and transport networks as well as personal devices. WannaCry is a ransomware virus - it encrypts all of the data on computers it infects, with users only having their data decrypted after they had paid $300 or $600 ransom to the hackers. Users who have had their device infected can only see the screen below until they have paid the ransom. 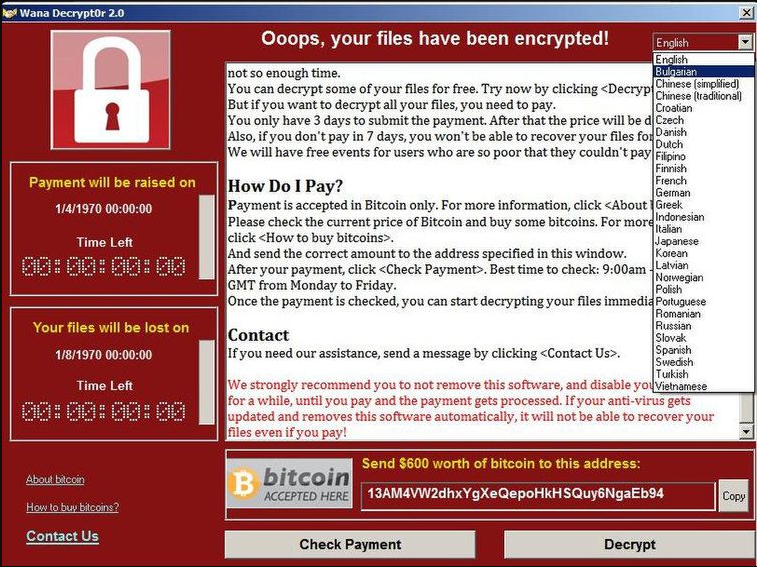
Source: CNN Money
In the first six days after the attacks, the hackers have received over USD$90,000 through over 290 payments (you can track the payments made to the known Bitcoin wallets here via a useful Twitter bot created by @collinskeith), which isn’t a fantastic conversion rate considering they managed to infect over 200,000 computers. Perhaps if the hackers had done their market research they would have realized that their target audience - those still using Windows XP - are more likely to still write cheques than pay for things with Bitcoin.
The attack was enabled by tools that exploit security vulnerabilities in Windows called DoublePulsar and EternalBlue. These tools essentially allow someone to access every file on your computer by avoiding the security built into your operating system. The vulnerabilities were originally discovered by the National Security Agency (NSA) in the US, but were leaked by a hacker group called The Shadow Brokers in early April 2017.
The graph below, generated using the time series feature in our News API, shows how the coverage of ransomware and malware in articles developed over time. The Shadow Brokers’ dump in early April was reported on and certainly created a bit of noise, however it seems this was forgotten or overlooked by almost everyone until the attack itself was launched. The graph then shows the huge spike in news coverage once the WannaCry attack was launched.
Volume of articles mentioning “malware” or “ransomware” in April and May
Monitoring the Media for Warning Signs
Since WannaCry took the world by such surprise, we thought we’d dig into the news content in the weeks prior to the attack and see if we could find any signal in the noise that would have alerted us to a threat. Hindsight is 20/20, but an effective media monitoring strategy can give an in-depth insight into threats and crises as they emerge. By simply creating a list of the hacking tools dumped online in early April and tracking mentions of these tools, we see definite warning signs. Of these 30 or so exploits, DoublePulsar and EternalBlue were the only ones mentioned again before the attack, and these ended up being the ones used to enable the WannaCry attack.
Mentions of each of the exploit tools dumped in April and May
We can then use the stories endpoint to collect the articles that contributed to the second spike in story volumes, around April 25th. Digging into these articles provides another clear warning: the articles collected cover reports by security analysts estimating that DoublePulsar had been installed on 183,000 machines since the dump ten days earlier (not too far off the over 200,000 machines WannaCry has infected). Although these reports were published in cybersecurity publications, news on the threat didn’t make it to mainstream media until the NHS was hacked and hospitals had to send patients home. 
Story on the spread of DoublePulsar and EternalBlue in SC Magazine
Trends in the Coverage
As it emerged early on Friday morning that malware was spreading through personal computers, private companies and government organizations, media outlets broke the story to the world as they gained information. Using the trends endpoint of our News API, we decided it would be interesting to try and understand what organizations and companies were mentioned in the news alongside the WannaCry attack. Below you can see the most mentioned organisations that were extracted from news articles about the attack.
Organisations mentioned in WannaCry stories
The next thing we wanted to do was to try and understand how the story developed over time and to illustrate how the media focus shifted from “what,” to “how,” to “who” over a period of a few days. The focus on Friday was on the immediate impact on the first targets, like the NHS and Telefonica, but as the weekend progressed the stories began to focus on the method of attack, with many mentions of Windows and Windows XP (the operating system that was particularly vulnerable). On Monday and Tuesday the media turned then their focus to who exactly was responsible and as you can see from the visualization below mentions of North Korea, Europol, and the NSA began to surface in the news stories collected. Take a look at the chart below to see how the coverage of the entities changed over time.
Mentions of organisations on WannaCry stories published from Friday to Tuesday
Most Shared Stories about WannaCry
The final aspect of the story as a whole we focused on was how news of the threat spread across different social channels. Using the stories endpoint, we can rank WannaCry stories by their share counts across social media to get an understanding into what people shared about WannaCry. We can see below that people were very interested in the young man who unintentionally found a way to prevent the malware from attacking the machines it installed itself on. This contrasts quite a bit with the type of sources and subject matter of the articles from before the attack began. Facebook
- “The 22-year-old who saved the world from a malware virus has been named,” Business Insider. 33,800 shares.
- “'Accidental hero' finds kill switch to stop spread of ransomware cyber-attack," MSN.com. 28,420 shares.
- “Massive ransomware attack hits 99 countries,” CNN. 13,651 shares.
- “A Massive Ransomware 'Explosion' Is Hitting Targets All Over the World,” VICE Motherboard. 3,612 shares.
- “Massive ransomware attack hits 99 countries,” CNN. 2,963 shares.
- "Massive ransomware attack hits 74 countries," CNN. 2,656 shares.
- "'Accidental hero' finds kill switch to stop spread of ransomware cyber-attack," MSN.com. 24,497 upvotes.
- "WannaCrypt ransomware: Microsoft issues emergency patch for Windows XP," ZDNet. 4,454 upvotes.
- "Microsoft criticizes governments for stockpiling cyber weapons, says attack is ‘wake-up call’" CNBC. 3,403 upvotes.
This was a quick analysis of the media reaction to the WannaCry attack using our News API. If you’d like to try it for yourself you can create your free account and start collecting and analyzing stories. Our News API is the most powerful way of searching, sourcing, and indexing news content from across the globe. We crawl and index thousands of news sources every day and analyze their content using our NLP-powered Text Analysis Engine to give you an enriched and flexible news data source. 
Related Content
-
 General
General16 Feb, 2024
Why AI-powered news data is a crucial component for GRC platforms

Ross Hamer
4 Min Read
-
 General
General24 Oct, 2023
Introducing Quantexa News Intelligence

Ross Hamer
5 Min Read
-
 Product
Product15 Mar, 2023
Introducing an even better Quantexa News Intelligence app experience

Ross Hamer
4 Min Read
Stay Informed
From time to time, we would like to contact you about our products and services via email.
